Do you Know Pingbacks are Useful but Dangerous
Before we get into the topic, do you know what pingbacks are? Pingbacks are notifications that you see in your website’s comments section. They show that another website has linked back to your content such as the one show below:
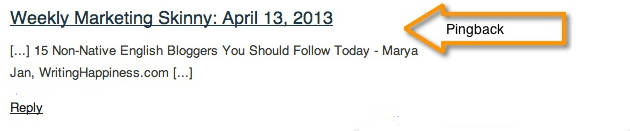
Good News…
If you are a WordPress user, then pingbacks come ‘enabled’ by default. This feature comes handy in monitoring inbound links. It is the source of building your reputation as a friendly and trustworthy content creator. If another website mentions your content with positive notes, you would also like other websites to know about it. You can make their post popular by sharing it on social networking sites.
As a result pingbacks can drive maximum traffic to your WordPress site (as a result of backlinks created on your content) and backlinks play a critical role in successful online visibility of a website.
That’s good news. But there are also dangers associated with it. What sort of dangers?
….Bad News
There is no guarantee that all mentions will turn out to be positive. There is a possibility that you will get negative feedback from internet users. But, you shouldn’t give up your good side and respond positively to negative comments.
However, such pingbacks can destroy your online reputation as well because WordPress uses an XML-RPC interface that can be vulnerable and can lead to DDoS (Distributed Denial of Service) attacks.
In simple terms, hackers can manipulate your website by sending innumerable pingbacks in a short period overloading your server and putting your website offline abruptly and resulting in expensive downtime and decreased conversion. Plus, you will be surprised to know that hackers can use pingbacks to uncover public IP addresses of a protected WordPress website and bypass DNS security.
And this is all due to the XML-RPC interface that WordPress uses for your website.
Now that we have covered the good and the bad, let’s try to protect your WordPress website from pingback vulnerabilities. But first, it is important to know whether your website has pingbacks enabled or not.
How to Check Whether Pingbacks are Enabled in your Website or Not?
Since the release of WorldPress 3.0 in 2012, XML-RPC interface comes enabled by default. Even after a decade, it has been a part of all the WordPress versions. But there is a possibility that when you created your WordPress website, the developer or if there is any other admin,might have ‘disabled’ this option. In either case, it is important that you verify whether pingbacks are ‘enabled’ or not.
For this purpose, our experts at WP-Bridge recommend the use of XML – RPC Validator tool:
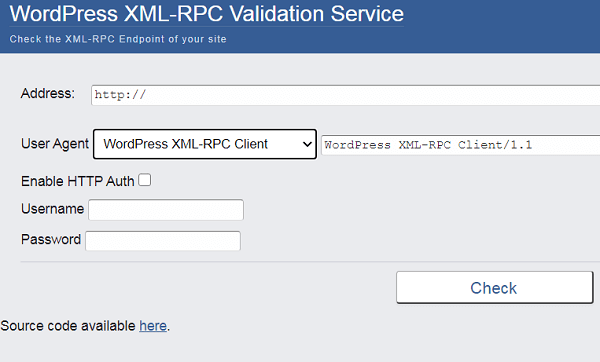
It’s super-easy to use this tool. You just enter your Website’s URL in the ‘address field’ and click ‘Check’. If this tool displays you an error message it means that XML-RPC is ‘disabled’. On the other hand, if you receive a success message, it means that XML-RPC is ‘enabled’.
Now comes the part where you need to ‘disable’ pingback in order to safeguard your website from pingback vulnerabilities. Let’s look at how you can do this, in the next section.
How to Safeguard your Site From Pingback Vulnerability of WordPress? - A Remedy
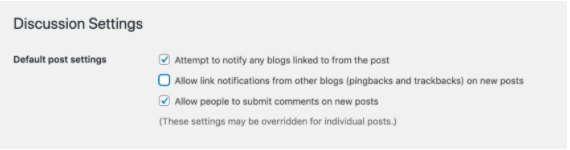
There are many ways you can ‘disable’ pingbacks. It is upto your discretion how and which part you want to ‘disable’. For instance, you can ‘disable’ pingbacks on all future posts.
Just go to Settings > Discussion in your dashboard and tick all options that you don’t want.
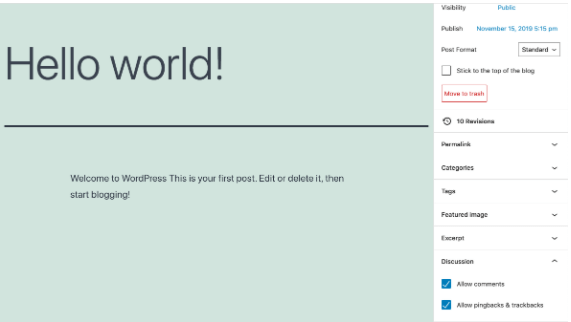
But if you want to ‘disable’ pingback for just 1 specific post, that is also possible. Go to the post editor for a certain post and disable pingback from there.
If you want to disable pingbacks throughout your website fully, following are three methods that will help you greatly depending on your skills and requirements:
Method # 1 - Use a Code Snippet to Turn off Pingbacks
Use of code snippets is the first method to resolve a technical glitch. If you’re thinking that, why are we starting with code snippets? Because using code snippets is an easiest way to not just fix pingback vulnerability but also you can add different functionalities in your WordPress site, that too without installing plugins.
Take a look at the image below showing how to add code snippets directly from your dashboard. Just log into your account, go to more Tools and go to code snippets (Tools > Code Snippets):
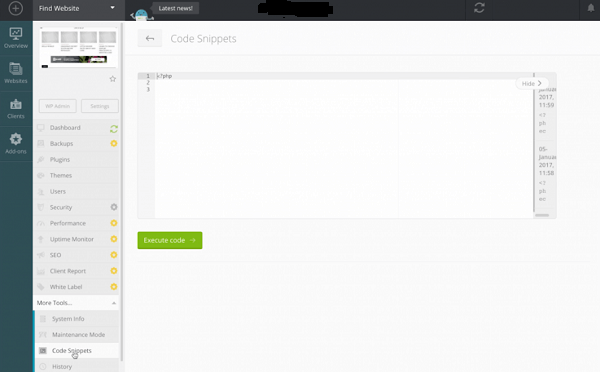
Now, you can paste code given below in your code snippet editor:
<?php
//Disable XML-RPC
add_filter('xmlrpc_enabled', '__return_true');
Alternatively, you can use another way to add snippets to your WordPress website. For this, you’ll have to add the ‘Code Snippets plugin’ : Activate this plugin, and navigate`(Snippet > Add New):
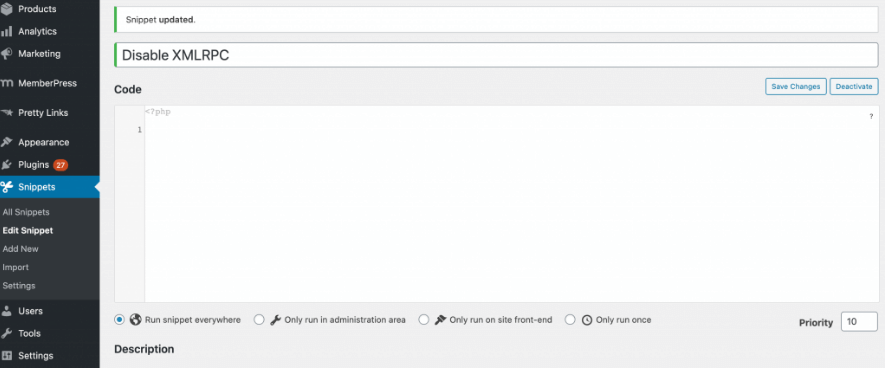
Copy and paste the snippet into the code editor given above. Now, click on Activate and check that XML-RPC is disabled through the use of XML-RPC validator
ADVICE: Our expert opinion is that you should also add a description defining what is the purpose of this snippet and why do you want to add it into your WordPress site. Believe it or not – it will ease up your life, especially, when you’ll revisit your code snippets next time. Plus, it optimizes transparency when you share your websites with collaborators.
Method # 2 - Try Manual Process for Disabling XML - RPC
Manually disabling XML – RPC is the second method that is useful. A website owner can block all incoming XML-RPC requests before they pass to the WordPress admin and create technical glitches.
In this method, you will have to edit .htaccess – a configuration file telling a server about how to deal with requests.
Important Advice: Take a full backup when you’re about to edit your .htaccess file. Because a simple mistake i.e., a typo can turn into a disaster while you’re editing a website’s code. With a backup, you will be at ease of restoring your lost files, in case, if some problems happen while editing your .htaccess file.
You are free to access .htaccess through FTP (File Transfer Protocol) clients such as FileZilla. Once you’ve got connected to your server, now locate .htaccess in your site’s root folder:
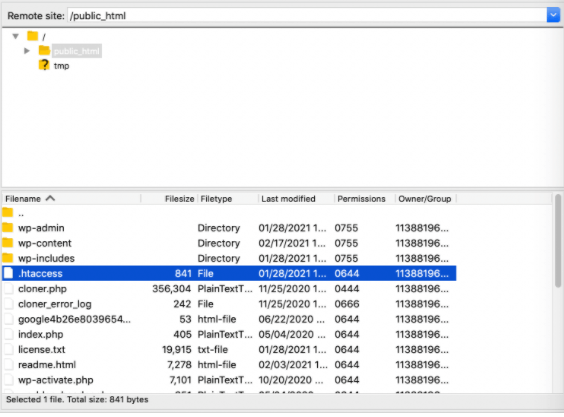
If you realize that the root folder has no .htaccess file in it, you’ll have to opt for force showing the hidden files option. After you have access to the file, open .htaccess in a text editor and add the following:
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
Now, save all of your changes. If you want to check whether your XML-RPC is disabled or not, try that XML-RPC Validator tool mentioned in this section again. And, now it should display an error message.
Method # 3 - A Plugin Can be Helpful for Disabling XML - RPC
In this final method, you’ll learn that there is a plugin that can help you disable XML – RPC. It is called Disable XML-RPC-API. Once you’ve installed and activated this plugin (Disable XML-RPC-API), it turns off pingbacks quickly without requiring further action. This plugin displays this confirmation message on the screen:
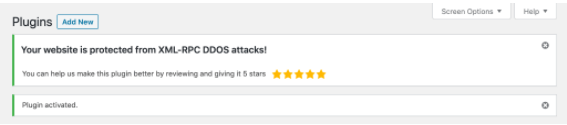
And, in case, if you want to turn XML-RPC again, just deactivate the plugin.
The Deciding Moment...Whether Pingbacks are Good for your WordPress Website or Not?
Although pingbacks are positives in most situations, they can be dangerous as they can lead to DDoS (Distributed Denial of Services) attacks in others. Plus, a successful DDoS attack can result in lost traffic, badly impacted online visibility, downtimes, and loss of lead generation and sudden decline in sales.
But there are ways around it that you can have the best of both the worlds. Do you want to know from experts about ways to protect your website against WordPress pingback vulnerability? Contact us now for more information for full protection of your WordPress website.
